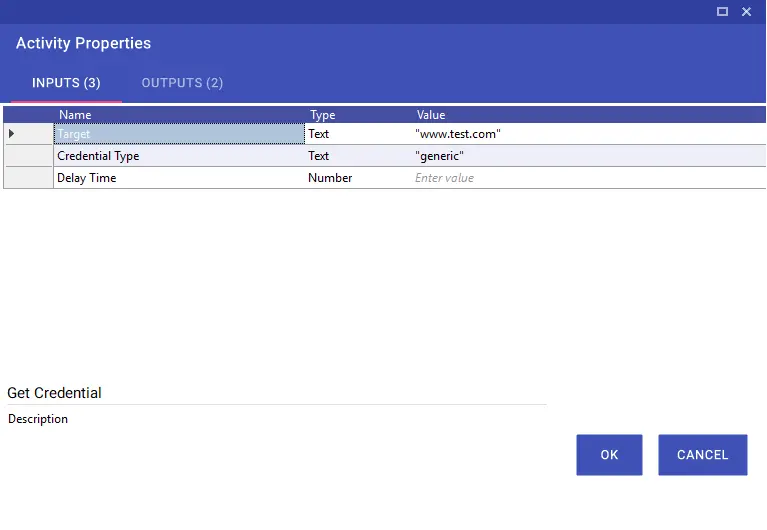
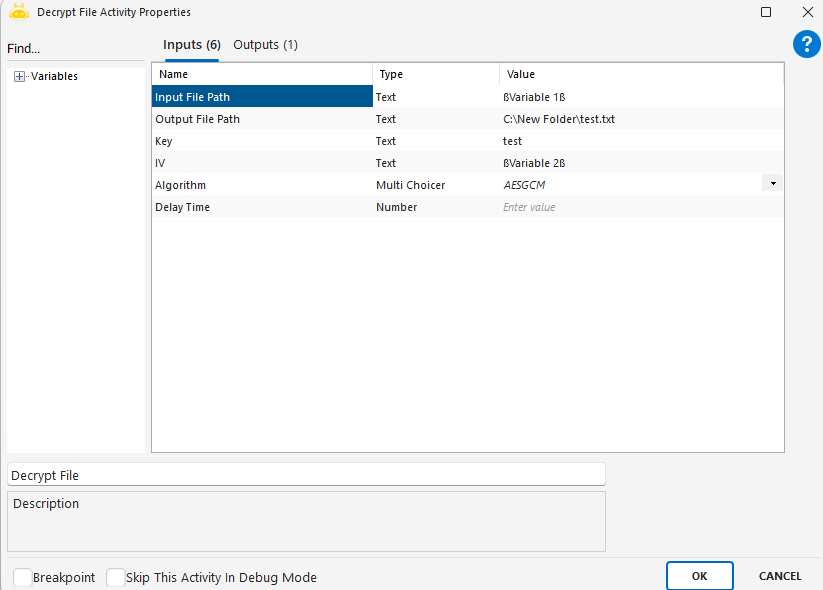
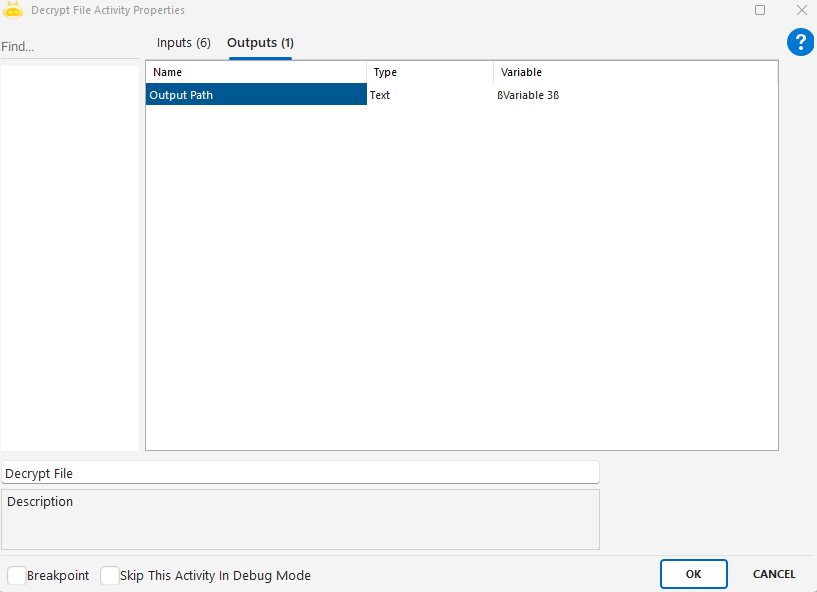
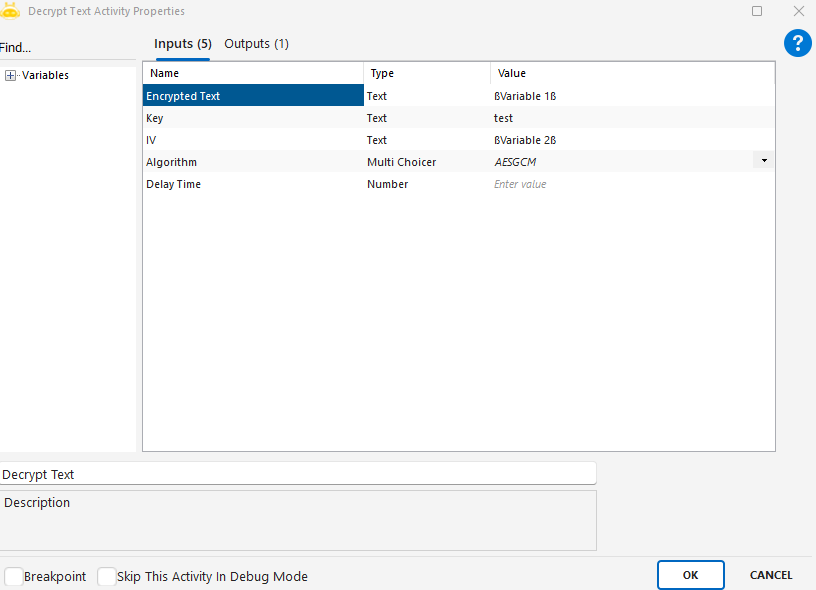
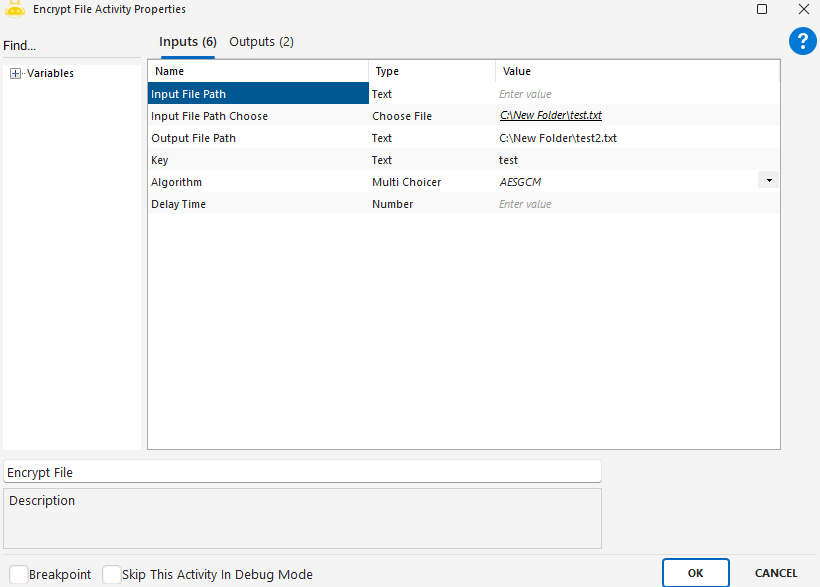
Encrypt File activity is used to encrypt the contents of a file using a specific algorithm and key. This ensures that sensitive files can be securely stored or transferred within an automation process.
Parameters:
InputFilePath: The full file path of the file to be encrypted.
InputFilePathChoose: Option to manually select the file via user interface (used in interactive applications).
OutputFilePath: The directory or full path where the encrypted file will be saved.
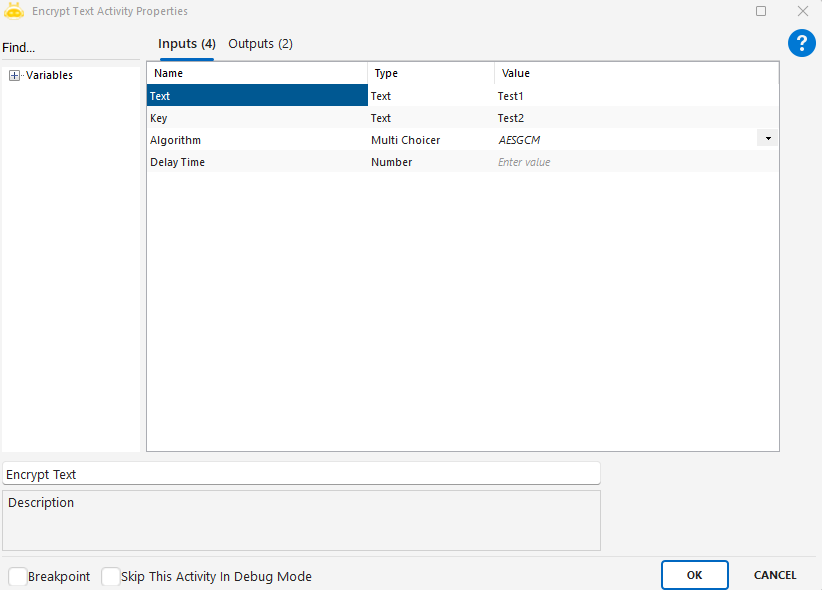
Key: The secure key used for the encryption process.
Algorithm: The encryption algorithm to be used (e.g., AES, DES, RSA).
DelayTime: The waiting time applied before or after the encryption process.
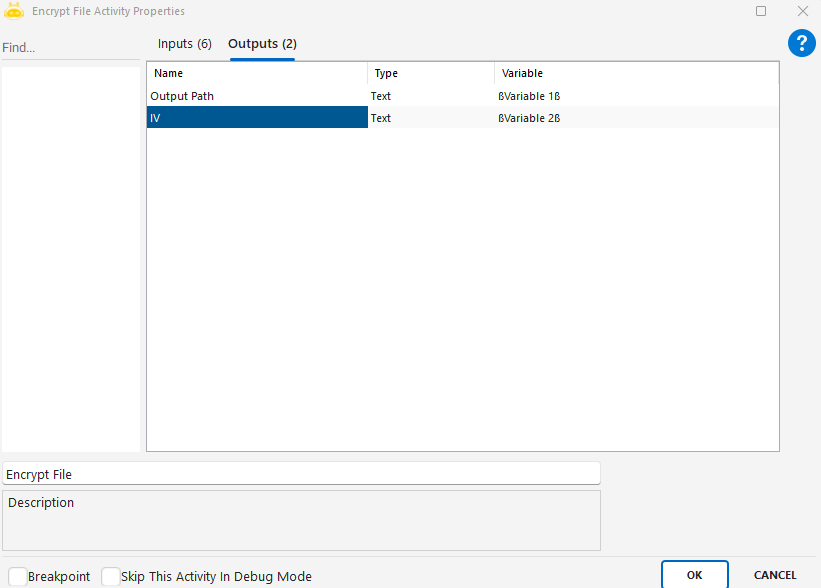
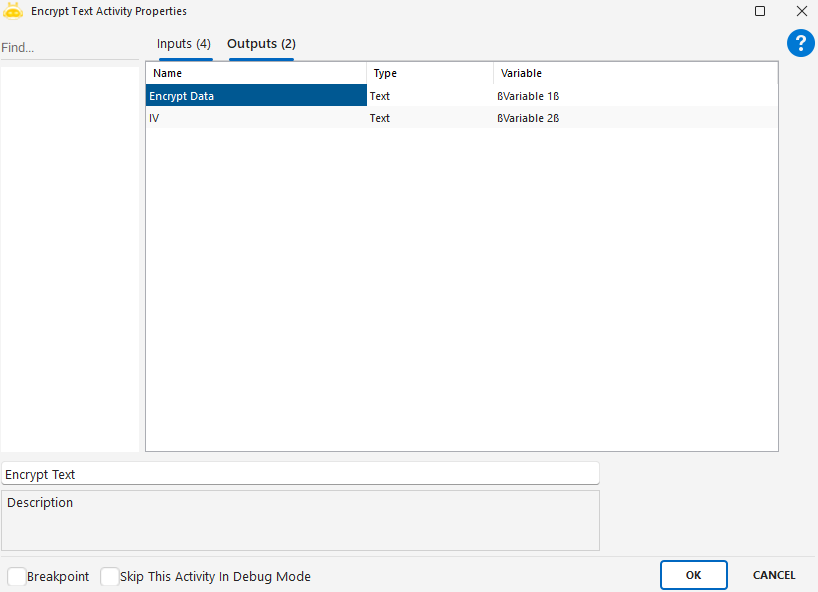
IV: Initialization Vector – an optional encryption value used for additional security.
Usage Scenario:
In an RPA process, the robot needs to securely store a generated report so that unauthorized users cannot access it. Therefore, the report file must be encrypted and saved to a specific directory.
InputFilePath: C:\Raporlar\GunlukRapor.xlsx
OutputFilePath: C:\SifreliRaporlar\GunlukRapor.enc
Key: my_secure_key_2024
Algorithm: AES
IV: 16byte_vector_123 (if required)
DelayTime: 500
After this process, the file is encrypted and securely stored for later use.